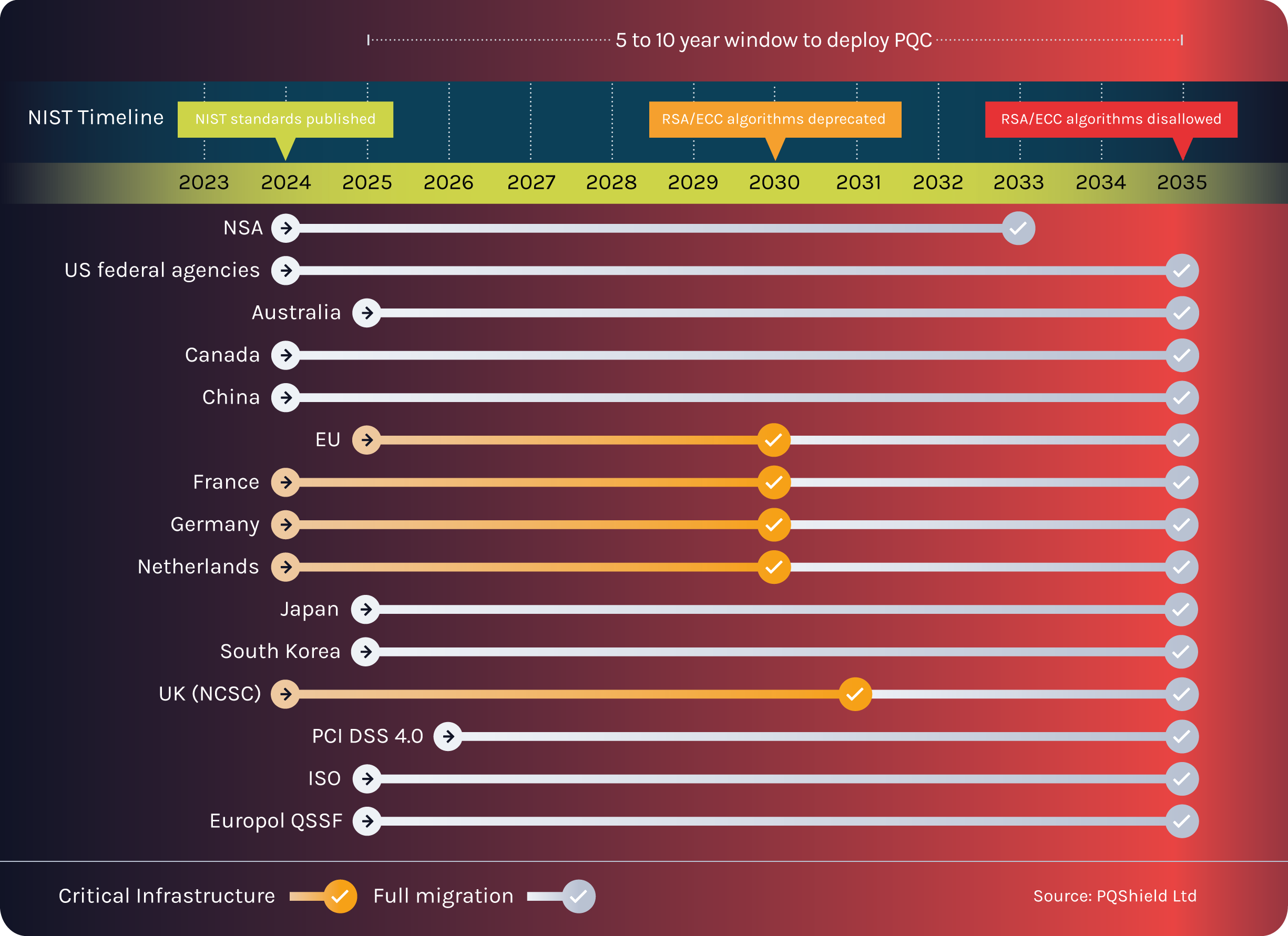
PQC Roadmaps and Transition Guidance
There’s little doubt that the era of quantum computing has already arrived. No longer a distant theoretical milestone, the advent of the quantum age has made post-quantum cryptography now a strategic imperative. The question is no longer if you need to transition to quantum-safe cryptography, but how and when.
This resource is designed to show a central view of how governments and agencies around the world are building compliance regulations to help navigate the shift to PQC.
CNSA 2.0
The Commercial National Security Algorithm Suite 2.0 (CNSA 2.0) (published in 2024) outlines requirements, algorithms and strategies for transitioning US National Security Systems (NSS) to quantum-resistant solutions. CNSA 2.0 provides a detailed roadmap for migration, with the goal of complete transition for all NSS to quantum-resistance by 2035.
Explicit milestones are specified for the following product categories to adopt CNSA 2.0 compliant algorithms:
- 2025: New software and firmware signatures
- 2025: Web browsers, servers and cloud servers
- 2026: Traditional networking equipment such as VPNs and routers
- 2027: New NSS, operating systems
- 2030: Legacy systems unable to support CNSA 2.0 phased out
- 2035: All NSS quantum-resistant
Canada's Roadmap for migration to PQC
Canada released its post-quantum cryptography roadmap in June 2025, outlining the Canadian government’s plan to transition non-classified IT systems to PQC with an end date of 2035. In the Government of Canada, ‘non-classified’ systems manage UNCLASSIFIED, PROTECTED A, and PROTECTED B information, and do not contain, transfer, or handle classified information. Users are recommended to contact the Canadian Centre for Cyber Security for more advice on handling PROTECTED C information.
Canada’s phased transition is based around a timeframe as follows:
- April 2026: Develop an initial departmental migration plan
- Beginning April 2026 (and annually thereafter): Report on PQC migration progress
- End of 2031: Completion of PQC migration of high-risk, high-priority systems
- End of 2035: Completion of PQC migration of remaining systems
EU Co-ordinated Roadmap
The EC (European Commission) initially released recommendations on a co-ordinated roadmap intended as a broad outline for Member States to prepare for, plan, and implement their transition to PQC. In June 2025, the first deliverable of the roadmap from the NIS Cooperation group, was published. The Roadmap on Post Quantum Cryptography sets out recommendations based around three milestones:
- 31 Dec 2026: Initial national transition roadmaps and first steps (identification and awareness)
- 31 Dec 2030: High-risk use cases and next steps implemented (resources allocated, pilots and upgrades PQC by default)
- 31 Dec 2035: Full transition (as much as is feasibly possible)
There is also a focus on standardized and tested hybrid solutions wherever suitable.
ENISA recommended cryptographic algorithms
The publication of ECCG’s Agreed Cryptographic Algorithms version 2 (May 2025) outlines guidance for developers, evaluators, decision-makers and users of cryptographic systems, and provides an overview of cryptographic mechanisms that are currently accepted by national cybersecurity certification authorities in Europe. In particular, following a risk-based approach, ENISA recommends, whenever possible, the use of symmetric mechanisms with adjusted parameter lengths and the adoption of PQ/T hybrid schemes, ensuring protection against potential vulnerabilities in newer post-quantum mechanisms. The European Commission, with the support of ENISA, also launched the Coordinated Implementation Roadmap leading to secure high-risk systems by the end of 2030 and full system transition to PQC by 2035.
NCSC Roadmap
In 2025, the UK’s National Center for Cybersecurity (NCSC) published a detailed roadmap and Next Steps in preparing for post-quantum cryptography including three distinct phases. It emphasizes a centrally-managed migration, avoiding the risks of a rushed and fragmented transition:
- Discover and plan (2028) – a full discovery exercise and inventory of vulnerable systems
- Prioritize and pilot (2028-31) – high-priority migration activity, critical systems and pilot in test environments
- Complete adoption (2031-35) – full PQC migration for all systems, services and products.
This three-phase focus on developing, implementing, and refining a robust plan for migration is important. The NCSC emphasizes that PQC migration should be done carefully, strategically, and without introducing new security risks. For this reason, the NCSC also provides a number of helpful stages for developing a plan, including an understanding of your current estate, prioritizing activities based on sensitive or most-valuable assets or data, and emphasizing testing and validation throughout.
Australian guidance on PQC transition
The core of the Australian government’s position to PQC migration is outlined in the Australian Signals Directorate (ASD) Information Security Manual. The mandate is that traditional asymmetric cryptography must not be used beyond the end of 2030 and that, according to to the ASD, organizations should develop a refined plan for transition by the end of 2026, with a view to commencing transition of critical systems and data by the end of 2028. This is set out in the context of the increasing vulnerability to quantum computing in the early 2030s as well as a focus on preventing ‘harvest-now-decrypt-later’ attacks.
Japan - Quantum Technology Innovation
Japan’s strategy for managing the quantum shift is essentially a dual-track approach – developing and implementing PQC and also pursuing QKD (Quantum Key Distribution) technology. On PQC, the Cryptography Research and Evaluation Committees (CRYPTREC) has been evaluating algorithms, leading to the publication of a number of guidelines, with a strong emphasis on the ‘2030 Cryptography Problem’. The Cabinet Office Quantum Technology Information page serves as central hub for information on Japan’s quantum technology strategy.