In today’s digital world, the integrity and security of computer systems has become a significant concern. With the evolution of more sophisticated threats to our data, our components and our devices, the way we approach digital security has changed too.
Secure boot is at the heart of cybersecurity. That’s because it’s the basic process that determines the way trusted devices power up – relying on a chain of digital signature verification steps to authenticate everything that’s subsequently loaded onto that device.
It’s certainly a topic that recurs often – especially in the post-quantum conversation.
Following the 2024 announcement of the first PQC NIST standards, and alongside other recommendations from security experts around the world, implementing quantum-safe secure boot has become a pressing concern for manufacturers, chip designers, and stakeholders. How do we best deploy secure boot at this foundational level? How do we comply with recommendations and guidance? How does all of this feed into crypto agility, and, is there a perfect solution?
In this article, we’re looking at these questions, investigating some of the issues and trade-offs currently in play with secure boot solutions. At PQShield, we’ve spent years thinking ahead, planning for the challenges of the quantum era. We’ve had a hand in co-authoring many of the international PQC standards, and we’ve also been building real-world, post-quantum, flexible solutions for the next generation of security threats.
The US guidance published in CNSA 2.0 mandates that in 2025, the first PQC use case should be software signing and firmware signing – exactly what’s required for secure boot, integrated into devices at the foundational semiconductor level of the supply chain. In reality, without secure boot, cybersecurity cannot be done.
That’s why the push is currently on for semiconductors. The trusted devices of the next ten or twenty years will rely on the technology that’s available at the root of the supply chain today. With long development cycles and supply chains, and the possibility that devices built today could have a long shelf life, the time for action is now.
Secure boot
Secure boot relies on digital signatures. The system firmware checks the digital signature of each component as it starts up. If the system detects an untrusted or unsigned component, it takes action, preventing the boot process. Essentially, users or manufacturers can control which keys are trusted by adding them to a list within the firmware – enabling administrators to define which ‘trusted’ code is allowed to execute during startup.
Quantum-safe secure boot replaces traditional public key algorithms like RSA and ECDSA with quantum-safe algorithms. But which algorithms should be used? And in what configuration?
It turns out that there are many things to consider, and there might not be a single solution for every secure boot use case.
Crypto agility and PQ/T hybrid schemes
One factor to consider has been the shift towards crypto agility. In essence, crypto agile thinking enables systems to switch rapidly, fix and patch quickly, and minimize the risk of migrating to new, less well-understood technologies without compromising operations.
For this reason, several (but certainly not all) governments around the world have mandated a PQ/T (post-quantum/traditional) hybrid approach. In this scheme, the power of post-quantum technology is combined with traditional algorithms such as RSA, DSA, and ECC. The following table shows how different players around the world currently view the use of hybrid schemes.

Evidently, there are trade-offs to take into consideration:
- PQ/T hybrid increases latency: instead of doing just post-quantum verification (for example ML-DSA), the system has to also execute RSA verification, doubling the latency.
- Double transition: crypto agility means transitioning into a PQ/T hybrid model and then potentially switching again to full PQC
- Context: for example, PQ/T hybrid could be more useful for systems with lots of interdependencies and external endpoints, but closed systems (such as defence networks) can migrate more easily to PQC.
A choice of algorithms
In addition to the choices around crypto agility, there are also considerations for different selections of algorithms.
While Europe recommends a hybrid approach, there are exceptions. Hash-based signature schemes (HBSS), which are very well understood, are also viable solutions to the PQC secure boot question.
France and Germany state that these schemes can be used directly without hybrid. However, as this table shows, CNSA 2.0 precludes the use of FIPS 205 SLH-DSA, indicating that the market to the US is likely to be closed to this option.
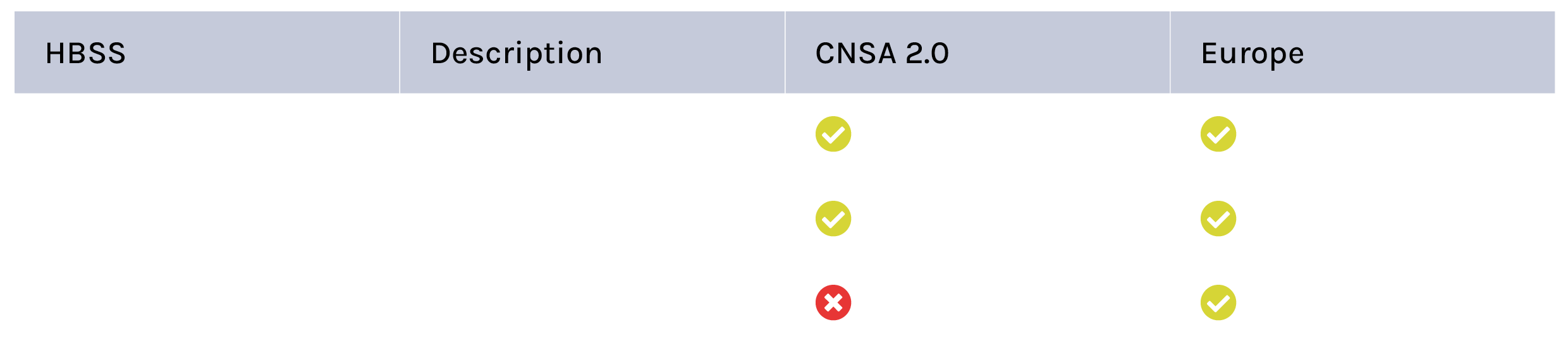
Meanwhile, the hash-based algorithms LMS and XMSS are ‘stateful’ rather than ‘stateless’. This means that key-pairs generated in the signature are ‘one-time only’, making it impossible to back up the state, or guarantee that a key pair won’t be regenerated. For secure boot, this is a significant vulnerability, as it opens the door to a signature being forged, opening the door to an attack. In addition, not being able to back up the state, means that if the key is lost, no further software update would be possible for that device.
Some vendors have certainly proposed new ways to backup the state, and eventually this will need to be certified by NIST and others, before being put into use. However, signature generation is only part of the puzzle when it comes to secure boot.
The supply chain
As well as generating signatures, there also needs to be a robust user authentication mechanism for trusted devices – determining who is able to use the key to update the firmware.
Typically this is done by two-factor authentication, the security of which is implemented at the semiconductor layer. The technology would need to be FIPS 140-3 CMVP Level 3 or 4 certified, and at present these standards are not yet forthcoming for PQC.
The fact that there’s no end-to-end solution is certainly causing a bottleneck. With the criticality of secure boot at the foundational layer of cybersecurity, there’s little doubt that collaboration is needed from various sources to provide a solution.
What can PQShield offer?
It’s important to note that cryptography has always been about risk mitigation rather than complete elimination of threat. That’s an encouraging way to think about secure boot because there are certainly things that can be done now to help mitigate the coming risks from quantum attack, even if first-stage secure boot at the semiconductor layer is much harder to implement.
In simple terms, our team of world-class PQC engineers have built a toolkit that consists of both hardware and software building blocks that can be combined in various ways to fit a use case to help defend against some of those risks.
The focus of our IP is its flexibility, and our security suite of products is highly optimizable for the unavoidable tradeoffs such as power, security, cost, and algorithm choice.
PQCryptoLib-Embedded for example, can be compiled and optimized for, say, low memory footprint for an embedded device. It contains a combination of post-quantum and classical algorithms in a cryptographic library. There are different optimization tradeoffs that can be achieved to make use of different hardware accelerators, making processing much faster. There is a wide variety of tradeoffs that this product can accommodate.
This is evidently applicable to second-stage boot loaders and above, the initial first stage boot being required in silicon, as described above. However, it is timely to implement this as it adds post-quantum cryptography to the communications layer of the device.
When it comes to designing the next generation hardware layer, our PQPlatform family of products can be optimized for low area footprint and high security – which is exactly what’s required for secure boot.
PQPlatform can be built from several building blocks.
- PQPlatform-Hash: Low footprint IP that delivers hash-based signature schemes
- PQPlatform-Lattice: Accelerates and implements lattice-based algorithms such as ML-DSA and ML-KEM
- PQPlatform-CoPro: Combines lattice-based and hash-based signature schemes
- PQPlatform-SubSys: Autonomous subsystem which has no load on an existing CPU
- PQPlatform-TrustSys: (in development) Delivers full root-of-trust PQC
In addition, we’ve also built PQPerform, which is designed specifically for fast performance. Its high speed comes with the trade off of a larger area, but it’s much faster than anything on the market.
To find out more about PQShield products, view the products page, where you’ll find white papers on secure boot and other topics, as well as more detailed information on our products.
View our video here
Contact us for more information.

