The Quantum Threat
The invention of quantum computing could be another significant leap in technology, projecting us forwards into a new era of growth and progress. It also presents a serious cybersecurity threat to embedded systems everywhere.
A quantum computer leverages the principles of quantum mechanics to generate enormous computational power that classical supercomputers are unable to do. As a result, they could be able to solve specific problems, like complex modelling required for drug discovery or the creation of energy-efficient systems and processes.
However, quantum computers could also be used to break a very different kind of problem – the mathematical techniques that currently keep our online data safe in traditional Public Key Cryptography.
Public Key Cryptography algorithms rely on mathematical “trapdoors”, operations that are easy to apply, but difficult to undo without additional information. The central idea is that a public key lets you apply the trap door (encrypt), and only the corresponding private key enables you to safely decrypt. Without the private key, the information remains secure because the mathematical problem is too difficult to solve.
In the 1990s, mathematicians began developing new techniques to figure out how to solve some of these ‘hard’ problems. Peter Shor’s algorithms were major breakthroughs, showing for the first time that there is a path to breaking public-key cryptography. To run Shor’s algorithms, a computer would require a vast amount of processing power – far more than is possible for any classical computer.
Now, the rapid advancements in quantum computing mean the public key schemes that protect our embedded systems today, such as RSA and ECC, are at risk of being broken soon.
NIST Standardization
As a result of the quantum threat, the field of post-quantum cryptography (PQC) has emerged – a community of academics, researchers, engineers and organisations, with a view to updating cryptography to quantum resistance.
In 2016, the United States National Institute of Standards and Technology (NIST), launched the formal process to develop and standardise a set of post-quantum algorithms, submitted by the post-quantum cryptography community.
The aim was to evaluate various PQC candidates for two primitives:
● key agreement (which includes key exchange, public key encryption and key encapsulation mechanisms, or KEMs)
● digital signatures (providing authentication, integrity, and non-repudiation of a digital message)
In 2024, after three rounds of candidates, NIST announced that the following three post-quantum algorithms would be standardised as FIPS 203, FIPS 204, and FIPS 205.
● FIPS 203 ML-KEM (Kyber) Module-Lattice-Based Key-Encapsulation Mechanism Standard
● FIPS 204 ML-DSA (Dilithium) Module-Lattice-Based Digital Signature Standard
● FIPS 205 SLH-DSA (SPHINCS+) Stateless Hash-Based Digital Signature Standard
In addition, the following algorithm is also expected to be published in due course.
● FN-DSA (FALCON) Fast Nominative Digital Signature Algorithm
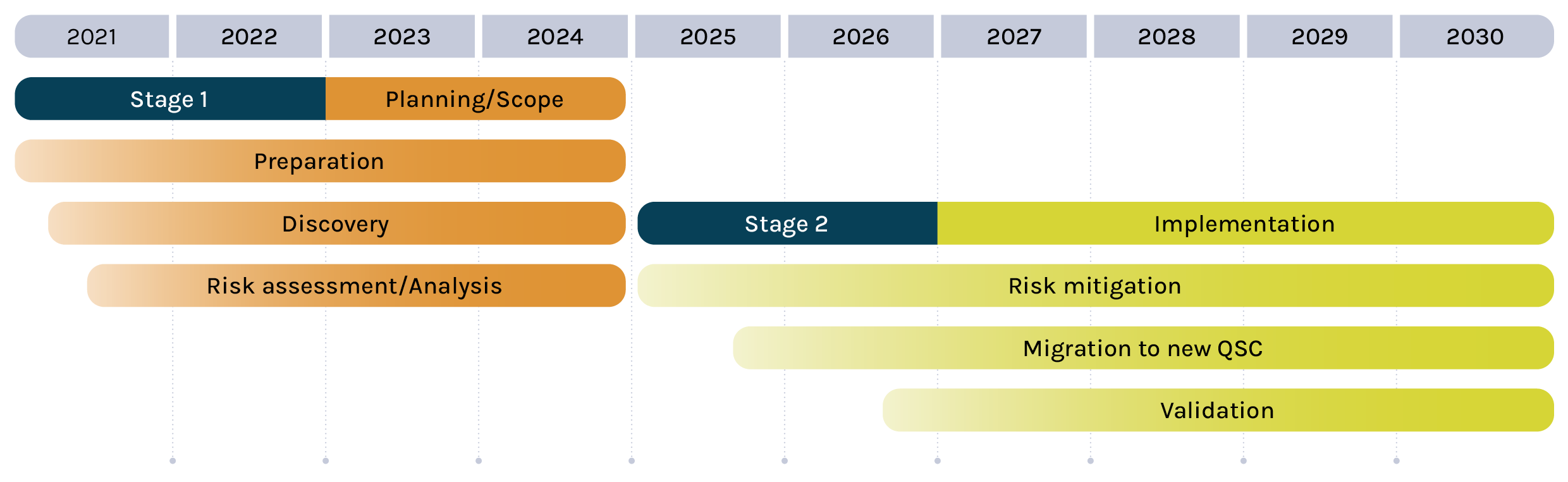
The publication of standards is a milestone in the story of PQC, and it’s certainly come at a point of transition in 2024. The following diagram, an example timeline recommended by the Canadian National Quantum-Readiness Working Group, shows how the shift from Stage 1 (preparation for migration) is impacting the conversation, shifting the focus to implementation and compliance (Stage 2).
Protecting Embedded systems
As NIST’s standards come into place, bring embedded systems into alignment with them presents a specific challenge.
Embedded systems are often specialised by design and support limited resources like memory and bandwidth. They can have long shelf-lives and be difficult to replace, and it’s possible that a device is susceptible to physical vulnerability, being remote or deployed in an accessible location.
As a result of these factors, embedded devices and systems can be particularly susceptible to threats, and efficiently upgrading their cryptographic protections might be more difficult than with general-purpose systems.
As industries move further towards PQC-compliance, the necessity to upgrade embedded systems increase. What migration strategies are already available to designers and manufacturers?
The regulatory landscape
The last few years have seen security bodies and agencies around the world take notice of the need to implement PQC – with the US government releasing key legislation for federal agencies (such as CSNA 2.0) and organisations such as the German Federal Office for Information Security (BSI), the UK’s National Cyber Security Centre and the French national security agency (ANSSI) releasing key guidance and timelines for migration.
The one consistent message across all the published guidance is clear, organisations should already be planning the transition to post-quantum cryptography, and for many governments, the time to begin implementation of PQC algorithms is now.
How can this be applied practically to embedded systems?
PQCryptoLib-Embedded
As the regulatory landscape and NIST standardisation efforts highlight, protecting embedded systems against quantum threats is an immediate concern for industries reliant on secure, long-lasting devices. PQCryptoLib-Embedded is PQShield’s response to this challenge, a state-of-the-art solution engineered to bring robust post-quantum cryptographic capabilities to memory-constrained environments. Designed to serve embedded systems with specific performance and resource limitations,
PQCryptoLib-Embedded is compatible with a wide range of embedded devices, including microcontrollers and architectures like ARM, RISC-V, and x86. It integrates key post-quantum algorithms such as ML-KEM, ML-DSA, and SLH-DSA, alongside other non-standard post-quantum and traditional cryptographic algorithms. This robust combination enables PQCryptoLib-Embedded to support encapsulation mechanisms, signature schemes, as well as symmetric and asymmetric encryption.
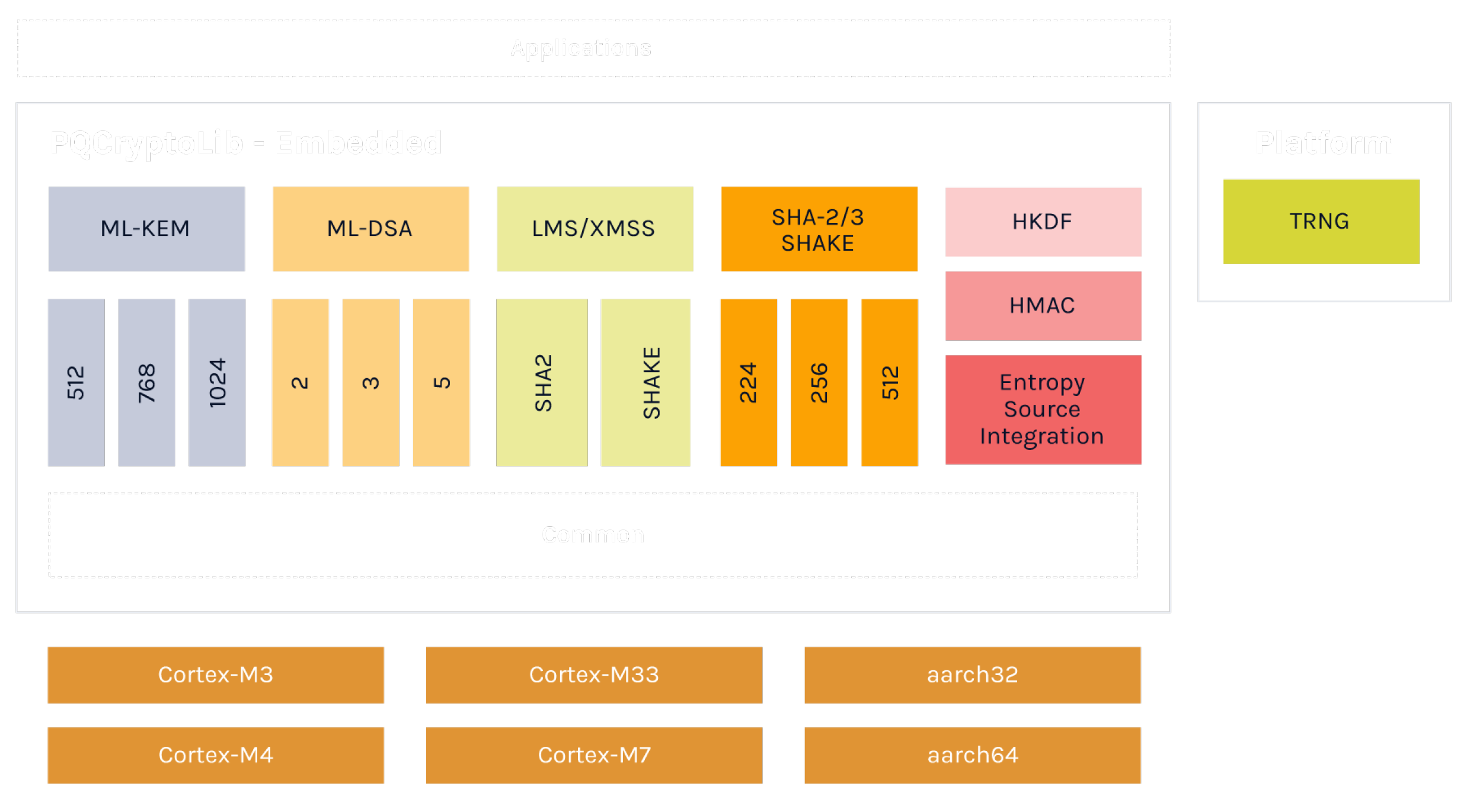
With its highly configurable architecture, PQCryptoLib-Embedded enables developers to select only the cryptographic functions they need, minimising binary size and optimising memory use—an essential strategy for devices with limited resources. This flexibility aligns with international cryptographic standards such as FIPS 140-3, covering FIPS 202, 203, and 204, to meet stringent security requirements across global markets and achieving FIPS ACVP and CMVP certifications, while respecting ISO standards for implementation.
In anticipation of potential vulnerabilities, PQCryptoLib-Embedded includes built-in defenses against attacks that exploit malformed inputs, offering a line of defense against adversarial manipulation. Additionally, the libraries are subjected to rigorous fuzz testing, a process that significantly reduces the probability of implementation bugs, further enhancing system resilience. PQCryptoLib-Embedded is also designed to be resistant to timing-based cryptanalysis, ensuring uniform execution times that avoid timing vulnerabilities. Moreover, the ML-KEM implementation within PQCryptoLib-Embedded undergoes formal verification on selected platforms, providing mathematically proven assurances of security.
Optimised for bare-metal environments, PQCryptoLib-Embedded supports deployment on hardware directly in baremetal, which maximises processing efficiency and reduces latency. This design is enhanced by the library’s ability to integrate with hardware hash engines, facilitating the offloading of hash calculations to dedicated hardware and boosting performance for hash-based signature schemes like LMS, XMSS, and SLH-DSA.
By including both quantum-resistant and classical cryptographic support, PQCryptoLib-Embedded offers an adaptable pathway toward secure, quantum-resistant infrastructure.
For industries that must balance security compliance with performance and memory constraints, PQCryptoLib-Embedded provides a foundation for long-term resilience, addressing the pressing needs raised by new regulations and standards.
Build securely
Quantum computing presents a fundamental risk to our traditional cryptographic methods, In every single industry, the cryptography that keeps data, devices, connections, and components secure, needs to be modernized in order to align with the new global standards. This modernization needs to begin today.
As businesses embargo on their journey to quantum security, they must remember to think openly and build securely. Through products like PQCryptoLib-Embedded, organisations can adopt quantum-resistant, FIPS-ready cryptographic solutions to update the legacy cryptography components of the world’s technology supply chain, and staying one step ahead of the attackers.

