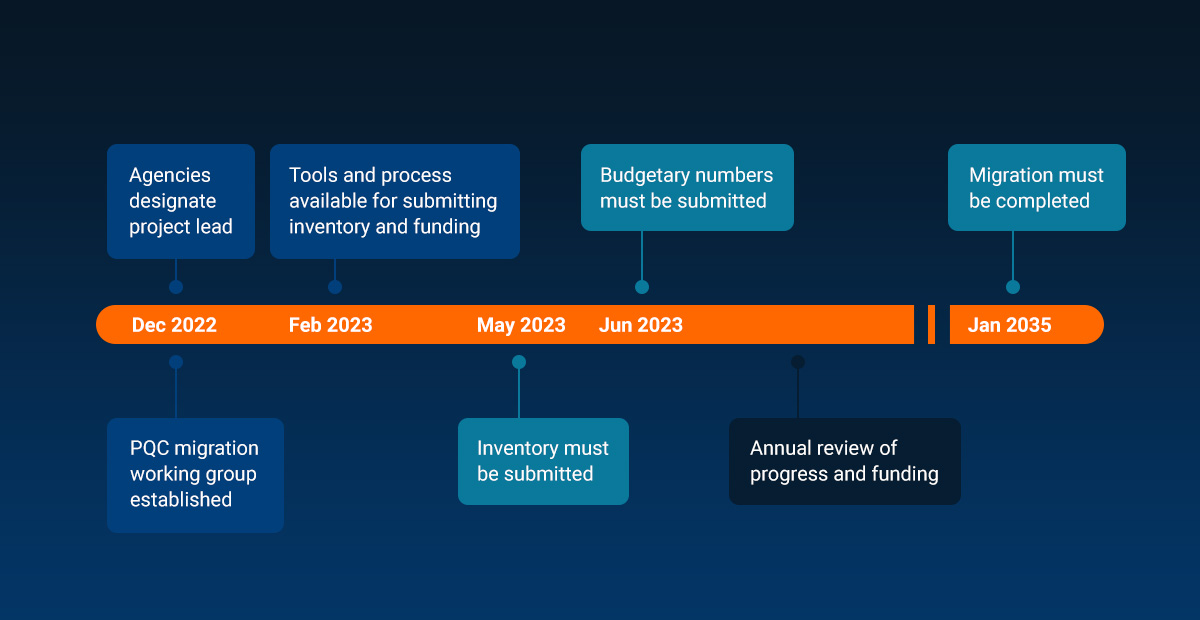
On November 18, 2022, the Director of the United States Office of Management and Budget (OMB) outlined the need for agencies and departments to migrate systems to post-quantum cryptography (PQC), in memorandum M-23-02
The subsequent legislation, H.R. 7535 was then signed into law on December 21st. It encourages the federal government to “adopt technology that is protected from decryption by quantum computing” as well as outlining regulations on software procurement, standardization for testing, and training (H.R. 7776).
In this article, we explain more about what exactly this means – not just for the US Government, but for any public enterprise aiming to migrate cryptographic systems to quantum-resistance.
As an organization, you’ll need to understand the scope (inventory), the cost (funding), and the priorities (impact) of migrating your cryptographic systems.
Build a prioritized inventory
Within the first six months, agencies are required to submit an inventory of all cryptographic systems, as directed by NSM-10. The aim of this first step is to understand which systems are impacted, and to prioritize their migration to PQC. A cryptographic system is defined as any implementation that involves:
- Creation and exchange of encryption keys
- Encrypted connections
- Creation and validation of digital signatures
Systems using any of the following algorithms could be at risk from a potential cryptographically relevant threat:
- ECDH key exchange
- MQV key exchange
- ECDSA
- Diffie-Hellman key exchange
- RSA
- Digital Signature Algorithm
You need to understand how your systems use cryptographic solutions before you can establish which are a priority for migration. The decision should be based on the potential risk to high-value assets or to information that would have a high impact if compromised.
For off-the-shelf systems, this might mean engaging with your vendors to understand the best path to quantum-resistance. And completing your inventory may also involve interviews, code reviews or deep-dives into any system your organization is using.
For example, you might want to think about systems which include these technologies:
| Technology | How it works | Examples |
| Document Signing | A public key is used for secure validation of a document in a transfer of confidential information. | * Online banking transactions * Medical prescriptions * Digital signatures in a supply chain |
| Code Signing | Secure update and secure boot can authenticate the identity of software before being installed or booted on hardware. | * Military hardware * Mobile phones and other devices |
| Certificates and Websites | Trusted certificates enable access to URLs by authenticating HTTPS connections. | * Online banking * REST APIs |
| User and Machine Identities | Digital certificates signed by a trusted party bind the identity of a user or machine to a public key, so that the device/user can then access resources. | * Machine connecting to a physical network * User with smartcard/USB * Encrypted entry/access systems |
| Key Distribution and Key Exchange | Public keys and private keys are generated in unique ‘key pairs’. The public keys are shared and managed by a public-key server. A sender of a secret can use the recipient’s public key to generate a ‘secret key’ that can only be decrypted by the corresponding private key of the recipient. | * Multiple cloud networks * Encrypted database clusters |
We will be producing a more comprehensive document to guide you through this process by vertical, particularly in the context of whether a system is in-house or supplied by an external vendor.
What to include in your inventory
For US agencies, the OMB has also provided some additional guidelines about what to include in the submitted inventory. For example, they require a list of:
- FIPS-199 system categorisation (e.g. Low, Medium, High)
- Each potentially vulnerable cryptographic system that’s actively used by the information system or asset, including:
- Cryptographic algorithm used
- Service provided by the cryptographic system
- Length of associated cryptographic keys or modules
- Operating system, including version numbers
- If part of a package, whether that package is commercial off-the-shelf (COTS), government off-the-shelf (GOTS) or from another vendor
- Hosting details – whether the system is hosted on premise or in the cloud, and details of the host
- Product lifecycle details – for example, how long the system might need to be in use
It’s a good idea to be as detailed as possible in your inventory, as this enhances your ability to test, report, and prioritize effectively. The principle applies to any organization preparing systems for PQC: it is critically important to know which systems will need to be migrated first.
The US agency deadline for submitting inventories is May 4, 2023.
Assessing the funding required
It’s also important to quantify the costs of migrating systems to PQC. US agencies must do this within 30 days of submitting an inventory, and it is a good idea to assess costs as soon as possible. This ensures that the budget can be accurately forecast and funding assessments approved, based on the most up-to-date inventory. You should also involve supply chain vendors where appropriate, as they might be able to support cost estimates.
Policy assistance is available for US departments, from the OMB Office of the Federal Chief Information Officer.
Plan for annual checks
In 2022, the NSA issued advice that national security systems must adopt the use of post-quantum algorithms by 2035. However, in the near term, the following applications must use quantum-resistant public-key algorithms:
- By 2025
- Software and firmware signing
- Web browsers/servers and cloud services
- By 2026
- Traditional networking equipment
With this timeline in mind, agencies and other organizations should take note of the guidance sooner rather than later. For US departments, this means repeating the process and submitting a prioritized inventory each year, on or before May 4, until 2035.
Even for non-government organizations, this timeline is incredibly significant as full migration of all systems is expected to take a long time. Taking an annual inventory of systems and mapping prioritization allows you to prevent against the very real threat of a ‘harvest now, decrypt later’ attack. It also gives you an up-to-date picture of which systems are currently at risk and when they will need to be replaced or updated.
A number of strategies could be effective. For example, many organizations already have a well-defined map of products, tools and systems, and will be aware that their assets are a combination of both in-house and vendor-supplied systems. One early step could be to start the PQC conversation with your vendors to understand their own migration to quantum-resistance. There’s a good probability that their responses will help to shape your strategy, as well as their own.
For in-house systems, you could consider choosing one specific area within a system to explore and experiment with migration. This approach will enable your team to focus on specific requirements from the beginning of the process.
Either way, determining the highest priority systems is essential. The key message from the memorandum is that all of us need to start testing our systems against quantum threats as soon as possible.
Whether a US agency or a public or commercial enterprise, the development of cryptographically relevant quantum techniques will impact us all. And over the next few years, there is no sensible choice but to get ahead by getting started.
How can PQShield help?
At PQShield, we have the expertise to guide you through the preparation for your migration. We’re the largest commercially assembled team of PQC specialist cryptographers, and we’re actively contributing to the standards that are shaping the future of post-quantum cryptography. If you’d like us to partner with you or lead your migration project, we’d be ideally positioned to help.
For further information, we recommend some of our published resources:
- Quantum Computing Threat: NIST POC standards are here… how can you keep ahead?
- How PQShield left its mark on every NIST algorithm
- PQShield announces major new customers, Microchip Technology and Collins Aerospace
- Secure Messaging in a Post-Quantum World
And if you want to find out more, we’d be more than happy to talk – get in touch with our team here.

